MASTER CYBER RESILIENCE
The A/CCRF certification is designed to test your theoretical knowledge of the NIST Cybersecurity Framework (CSF) and how to plan, manage, and optimize the framework for use within your own organization:
- The origin and original purpose of the framework
- The applicability of the framework across industries and sectors
- The three fundamental parts of the framework: the Core, the Implementation Tiers, and the Profiles
- The five functions (Identify, Protect, Detect, Respond, and Recover), the 23 categories (activities), and 108 subcategories (outcomes) under each of the five functions
- The purpose, utility, and intended use of the Implementation Tiers, Profiles, and Informative References
WHAT SKILLS WILL YOU LEARN?
- Framework Purpose and Its Origin: Explore the purpose and historical background of the NIST Cybersecurity Framework to better understand its objectives
- Framework Versatility: Discover the broad applicability of the NIST Cybersecurity Framework across diverse industries and sectors that make it universally acceptable
- Framework Components: Grasp the three fundamental parts of the framework (the Core, Implementation Tiers, and Profiles) and their interplay in cybersecurity planning and management
- Functional and Categorical Analysis: Gain comprehensive knowledge of the five functions (Identify, Protect, Detect, Respond, and Recover), the 22 categories (activities), and 106 subcategories (outcomes) that underpin the framework
- Practical Application and Framework Use: Comprehend the purpose, utility, and intended use of the Implementation Tiers, Profiles, and Informative References to translate theoretical knowledge into real-world application
-
Planning, Managing, and Optimizing: Develop the skills to effectively plan, manage, and optimize the NIST Cybersecurity Framework within your organization while ensuring its successful implementation and ongoing improvement

Starting your Cybersecurity Career Journey...
When you think about breaking into cybersecurity at an entry level or making a mid-career transition into GRC, it can feel like staring at a mountain.
Where do you start? What do you need to know? 🤔
One of the best guidebooks to begin with is the NIST Cybersecurity Framework (CSF). This 32-page document was first released 10 years ago in response to a presidential executive order and has been rapidly adopted since.
It’s remarkably effective at helping organizations of all shapes and sizes baseline their current state and establish an appropriate, tailored, desired state to become cyber resilient.
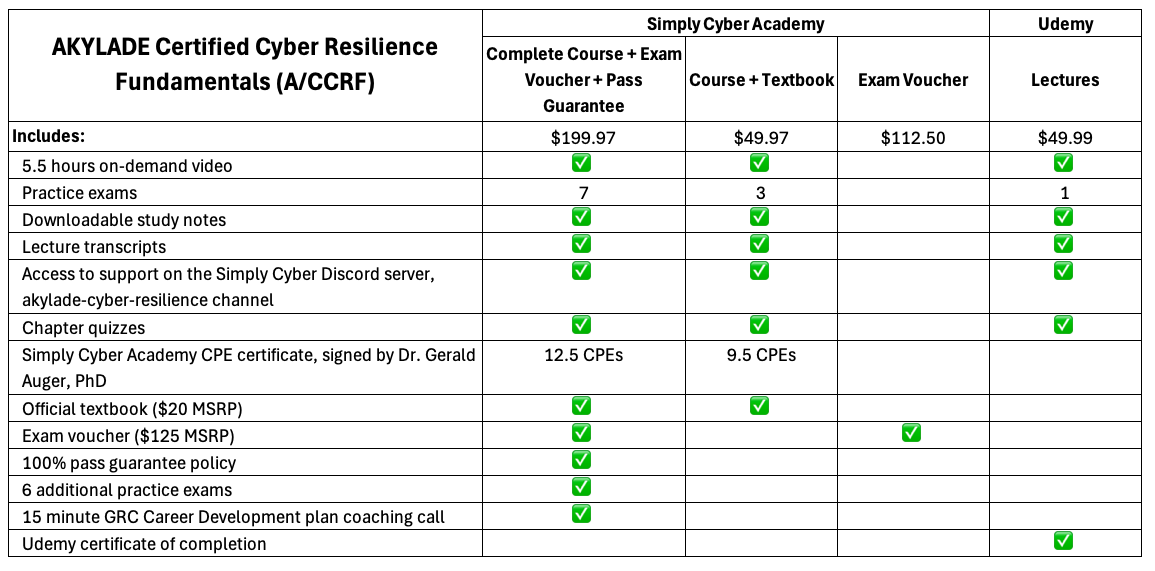
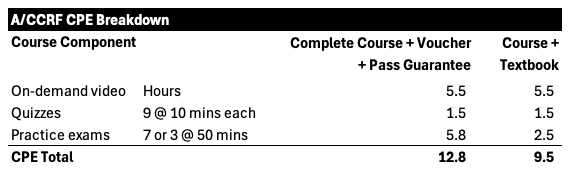
WHAT DOES THE COURSE INCLUDE?
This comprehensive course with everything you need to know to CRUSH the exam includes:
A New Certification Requested by Hiring Managers
Hiring managers in the AKYLADE Advisory Council identified CSF training as a key gap in the certification landscape.
While 22-46 year old certifications like Security+, CISSP, and CISA are valuable, they don't dive deep enough into the CSF to prepare you to add value from day one.
That's where the AKYLADE Certified Cyber Resilience Fundamentals (A/CCRF) exam and my course in Simply Cyber Academy come in, covering everything you need to know to pass it. 📚🎓

A/CCRF Exam Domains
-
Cybersecurity Framework Concepts (25%) 📖 Understanding the basics.
-
Framework Core (30%) 🔄 Six functions (Govern, Identify, Protect, Detect, Respond, Recover) drilling down into 22 categories and 106 subcategories. These enable effective communication about cyber risk between executives, managers, and practitioners.
-
Tiers (10%) 🏃 🚶 Determining the level of security based on your organization's unique mission, risk tolerance, and resources. CSF is not prescriptive and not one-size-fits-all. It is flexible and scalable.
-
Profiles (15%) 🧭 Strategic planning between current and desired states to align cybersecurity efforts with organizational goals.
-
Risk Management (20%) ⚠️ To reliably achieve objectives.
Mastering Cyber Resilience Curriculum
- 3.1 Introduction and Exam Objectives 📚️ (4:15)
- 3.2 Risk Management Fundamentals 🧱 (3:55)
- 3.3 Phase One: Risk Identification 🔍️ (4:13)
- 3.4 Phase Two: Risk Assessment ⚖️ (7:30)
- 3.5 Phase Three: Risk Response Planning 📋️ (4:33)
- 3.6 Phase Four: Risk Mitigation 🛡️ (5:52)
- 3.7 Phase Five: Risk Monitoring and Review 📉 (0:53)
- 3.8 Inherent Risk and Residual Risk ⚠️ (2:27)
- 3.9 Business Impact Analysis (BIA) 💥 (6:53)
- 3.10 Financial Analysis 📊 (1:36)
- 3.11 Quiz 📝
- 3.12 Conclusion and Touchpoints ✅ (0:42)
- 4.1 Introduction and Exam Objectives 📚️ (3:32)
- 4.2 Development of the NIST Cybersecurity Framework 🛠️ (5:27)
- 4.3 Relevant Executive Orders and Regulations 📜 (3:24)
- 4.4 Applicability of the Cybersecurity Framework 🌎️ (5:18)
- 4.5 Characteristics of the Framework 📏 (5:47)
- 4.6 Cyber Resilience 💪 (1:37)
- 4.7 Critical Infrastructure ⚙️ (2:21)
- 4.8 Intended Audience & Purpose of CSF 👥 (2:01)
- 4.9 Quiz
- 4.10 Conclusion and Touchpoints ✅ (1:34)
- 7.1 Introduction and Exam Objectives 📚️ (2:52)
- 7.2 Controls 🔒️ (1:29)
- 7.3 Voluntary Nature of the NIST Cybersecurity Framework 🙋 (4:42)
- 7.4 Outcomes 📈 (5:27)
- 7.5 Informative References 📖 (2:33)
- 7.6 ISO/IEC 27001 and 27002 (1:36)
- 7.7 NIST Special Publications (2:45)
- 7.8 CRI (0:44)
- 7.9 CIS CSC (0:55)
- 7.10 COBIT 5 (1:05)
- 7.11 ITIL (1:17)
- 7.12 PCI DSS (1:00)
- 7.13 HIPPA (1:39)
- 7.14 NERC CIP (1:10)
- 7.15 FedRAMP (1:12)
- 7.16 STAR (0:53)
- 7.17 OWASP (0:59)
- 7.18 Quiz
- 7.19 Conclusion and Touchpoints ✅ (0:41)
- 9.1 Introduction and Exam Objectives 📚️ (1:53)
- 9.2 Profiles 🛤️ (3:04)
- 9.3 Creating a Profile 🎨 (6:48)
- 9.4 Profile Tailoring 🪡 (10:09)
- 9.5 Sector-Specific Profiles 🏭️ (0:38)
- 9.6 Cyber Risk Institute (CRI) Profile (2:02)
- 9.7 Manufacturing Profile (5:50)
- 9.8 Election Infrastructure Profile (2:23)
- 9.9 Hybrid Satellite Networks Profile (2:23)
- 9.10 Smart Grid Profile (1:02)
- 9.11 Connected Vehicle Profiles (1:28)
- 9.12 Payroll Profile (1:06)
- 9.13 Maritime Profile (1:15)
- 9.14 Communications Profile (1:23)
- 9.15 Profiles and Regulatory Compliance 🔍️ (3:05)
- 9.16 Secure Once, Comply Many ✔️ (3:27)
- 9.17 Quiz
- 9.18 Conclusion and Touchpoints ✅ (2:16)
- 10.1 Introduction and Exam Objectives (2:16)
- 10.2 Case Study: Meeting Our Client 🤝 (2:20)
- 10.3 Identifying Threats ⚠️ (2:17)
- 10.4 Identifying Vulnerabilities 🐞 (2:42)
- 10.5 Identifying Risks 📊 (1:54)
- 10.6 Risk Mitigation Recommendations 🛡️ (2:45)
- 10.7 Benefits and Trade-offs of Risk Mitigations ⚖️ (3:04)
- 10.8 Evaluating Effectiveness 🔍️ (1:51)
- 10.9 Risk Management Plan 📍 (1:44)
- 10.10 Cybersecurity Strategy ♟️ (2:35)
- 10.11 Quiz
- 10.12 Conclusion and Touchpoints ✅ (2:11)
About Your AKYLADE Authorized Instructor, Steve McMichael, CCRP
Authorized AKYLADE instructor Steve McMichael from Simply Cyber Academy is committed to helping you accelerate your cybersecurity career.
Steve is passionate about guiding students from backgrounds as diverse as accounting, into cybersecurity GRC. He successfully made this shift himself and shares his journey in the popular blog, CPA to Cybersecurity. Exam prep courses for the AKYLADE Certified Cyber Resilience Fundamentals (A/CCRF) and AKYLADE Certified Cyber Resilience Practitioner (A/CCRP) are key parts of that journey.
Steve holds advanced degrees in business (BBA, MBA), along with top cybersecurity certifications (CCRP, CISSP, CISA), and is a Chartered Professional Accountant (CPA). With nearly 20 years of experience in tech, he currently serves as the Director of Governance, Risk, and Compliance at BlackBerry.
GRC | CAREER CROSSOVER | CERT PREP
Visit www.cpatocybersecurity.com to learn how to break into cybersecurity GRC. Already in? Elevate your GRC skills, methods and mindset.

Even More Simply Cyber Academy GRC Courses
Simply Cyber Academy is tailored to empower those seeking a rewarding career in GRC cybersecurity.



