3.1 Introduction and Exam Objectives 📚️
Exam Objectives 📚️
Understanding risk management is crucial before diving into the NIST Cybersecurity Framework. This chapter aims to provide a solid foundation in risk management, equipping you with the knowledge and terminology needed to navigate the complex landscape of cybersecurity.
By grasping these fundamentals, you'll be better prepared to identify, assess, and mitigate risks, ensuring the security and resilience of digital systems and assets.
Candidates must be able to understand the key concepts related to risk management. Students will be able to:
5.1 Explain the fundamentals of risk management
- Risk Analysis
- Qualitative
- Likelihood of Risk
- Impact of Risk
- Quantitative
- Single-Loss Expectancy (SLE)
- Annualized Rate of Occurrence (ARO)
- Hybrid
- Risk Appetite
- Risk Tolerance
- Business Impact Analysis
- Recovery Time Objective (RTO)
- Recovery Point Objective (RPO)
- Mean Time to Repair (MTTR)
- Mean Time Between Failures (MTBF)
- Single Point of Failure
- Mission Essential Functions
- Identifying Critical Systems
- Financial Analysis
- Total cost of Ownership (TCO)
- Return on Investment (ROI)
- Return on Assets (ROA)
5.2 Given a scenario, determine the appropriate risk response and to a given threat or vulnerability
- Risk Responses
- Acceptance
- Avoidance
- Transference
- Mitigation
- Types of Risk
- Inherent Risk
- Residual Risk
- Risk Register
5.3 Given a scenario, assess cybersecurity risk and recommend risk mitigations
- Identify threats to an organization
- Identify vulnerabilities to an organization
- Identify risks to an organization
- Recommend specific risk mitigations
- Determine benefits of a particular risk mitigation
- Determine the trade-offs of a particular risk mitigation
- Evaluate the effectiveness of a particular risk mitigation
- Develop a risk management plan
- Develop a cybersecurity strategy
Risk Management Fundamentals
Risk
Definition:
- The potential for loss, damage, or harm resulting from the occurrence of threats exploiting vulnerabilities in digital systems or assets.
So What?
- Cyber risk has catapulted higher in board room priorities, to become an existential business risk.
Risk Management
Definition:
- The systematic process of identifying, assessing, prioritizing, and mitigating potential risks to an organization’s digital systems, networks, data, and assets to ensure their confidentiality, integrity, and availability.
So What?
- Guard rails and due diligence to reliably achieve objectives. Not to slow you down. Consider that the fastest cars have the best brakes.
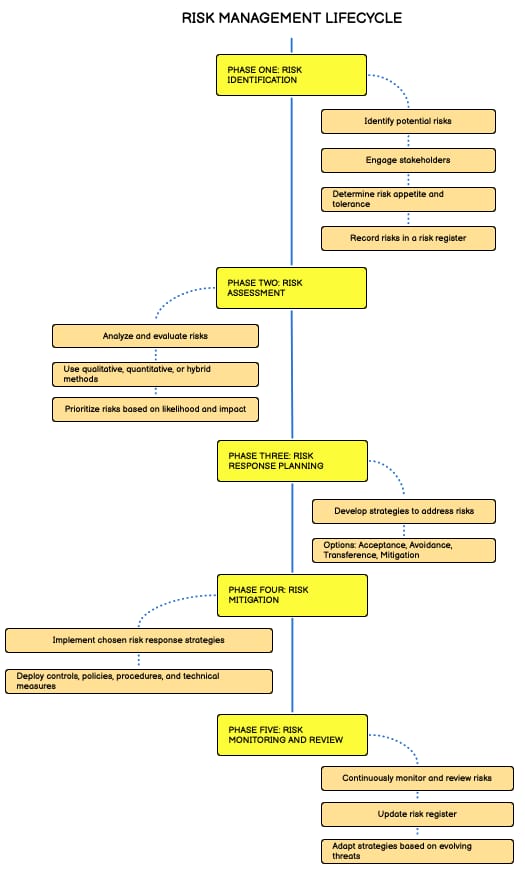
Risk Management Lifecycle
Definition:
- A systematic and iterative approach to managing risks by encompassing several phases.
So What?
- It’s a process, like Accounting
Risk Management Lifecycle
Risk management is a systematic process that involves identifying, assessing, prioritizing, and mitigating potential risks to an organization’s digital systems, networks, data, and assets. This process is essential for achieving cyber resilience. The risk management lifecycle provides a structured approach to managing risks through several phases:
Transcript
Risk management is one of my favorite topics, so I'm excited to jump into Mastering Cyber Resilience textbook chapter three, which relates to A/CCRF exam domain five, making up 20% of the exam.
Risk is the heart and center of Cybersecurity Governance Risk Compliance, GRC, which is what I do every day. And I’ve found that risk can be your superpower and opportunity to make an outsized impact, if you can learn to do it well and get a broad view of risk across the company. Then, while everyone else is focused on their specialized function, you are in a unique position to help the business prioritize where to focus, which can then help it reliably achieve objectives.
So let's jump right into the lesson. It says here, "Understanding risk management is crucial before we later dive into the NIST Cybersecurity Framework. That makes sense. In both accounting and cybersecurity, they use what they call a risk-based approach to control work, meaning you need to ensure that any controls you put in place are right-sized to the risk, or, what is the problem we're solving with controls? Let's just get clear on that first. Understand the risk.
“This chapter provides a solid foundation in risk management so that we can navigate the complex landscape of cybersecurity.” It's certainly a complex landscape. There's a lot of attack surface, and we need to be able to ruthlessly prioritize our security work, our resilience work. The first lesson objective in domain five is numbered 5.1, explain the fundamentals of risk management. Lots of terms and acronyms here. If you've done Security+, you've seen them before, but if you haven't, that's totally cool. That's why we're here, and we'll unpack each one. So you can join those Security+ and similar people to talk shop about likelihood, impact, RTO, TCO, and the rest on the page here.
Then in 5-2, it says, "Given a scenario, determine the appropriate risk response to a threat or vulnerability." And in 5-3, recommend some risk mitigations for that. So to illustrate what this is all about, let's just use a quick example.
If we take personal email, and our friends and family, maybe we run into Uncle Carl at a barbecue, and his risk response to email security is acceptance. He can't be bothered to use a password manager in MFA because he just says, "You know, I got nothing to hide. I'm not worried if someone gets into my email. I've got 99 other more important and urgent problems to deal with. I'm just gonna let it go. I'm going to sleep fine. I just accept that risk."
Now you might say, "Hey, Uncle Carl, something that a lot of people don't realize initially is that their online banking sends password reset emails to their personal email accounts. So personal email accounts are a juicy target for criminals that wanna steal your money. They get into your email, they pivot into your bank.
So another option you could consider here is avoidance. Just stop using email, don't allow those password resets to go to it from your bank, and you won't have to worry about hackers. Of course, then you won't have email. So maybe you want something else. Maybe you wanna do a transference strategy. So you could get a cyber insurance policy, and in the event that you have an email compromise and lose some money or some critical data or your identity, then from paying those premiums, you could then get a payout back from your insurance company to cover the cost and inconvenience you'd then have to go through should this happen.
Or if you don't like that option, we could talk about mitigations, and now we're back to password managers and MFA and think before you click training. So you get an idea here that there are different ways to address that risk of securing your personal email, whether you do it or whether you don't. You've got four options. And then we're also talking about some of the threats, the vulnerabilities, weak passwords, not having MFA. You could go really deep in this topic, but I'll keep it high level for now. Recommending options and determining trade-offs. How do we help Uncle Carl find the right balance that meet his needs? And that don't make him kind of unwittingly exposed to risks he might not know about.