7.3 Voluntary Nature of the NIST Cybersecurity Framework 🙋
Voluntary Nature of the NIST Cybersecurity Framework 🙋
Password Complexity Requirements
Is this secure?
A*QSuda@PxiTvwgDA2tG
https://bitwarden.com/password-strength/#Password-Strength-Testing-Tool

Other Options to Improve Authentication Security
- Multi-Factor Authentication (MFA): This method requires users to provide two or more verification factors to gain access to a resource such as an application, online account, or a VPN. Common factors include something you know (password or PIN), something you have (a smartphone or hardware token), and something you are (biometrics: fingerprint scans, facial recognition, or iris scans).
- Using Known Password Lists: Implementing checks against lists of known compromised passwords can prevent users from choosing passwords that are already exposed and easy to guess. This can be particularly effective in stopping common and repeated password-related vulnerabilities.
- Time-based One-time Password (TOTP): This is an algorithm that generates a one-time password which is valid only for a short period of time, providing an additional layer of security by ensuring that the password is not reusable.
- Geographic and IP Restrictions: Limiting access based on geographic location or IP addresses can help prevent unauthorized access from high-risk areas or unfamiliar sources.
- Anomaly Detection and Login Monitoring: Tools that monitor login attempts and detect anomalies (like logins from new devices or locations) can trigger additional authentication requirements or alerts.
Profiles
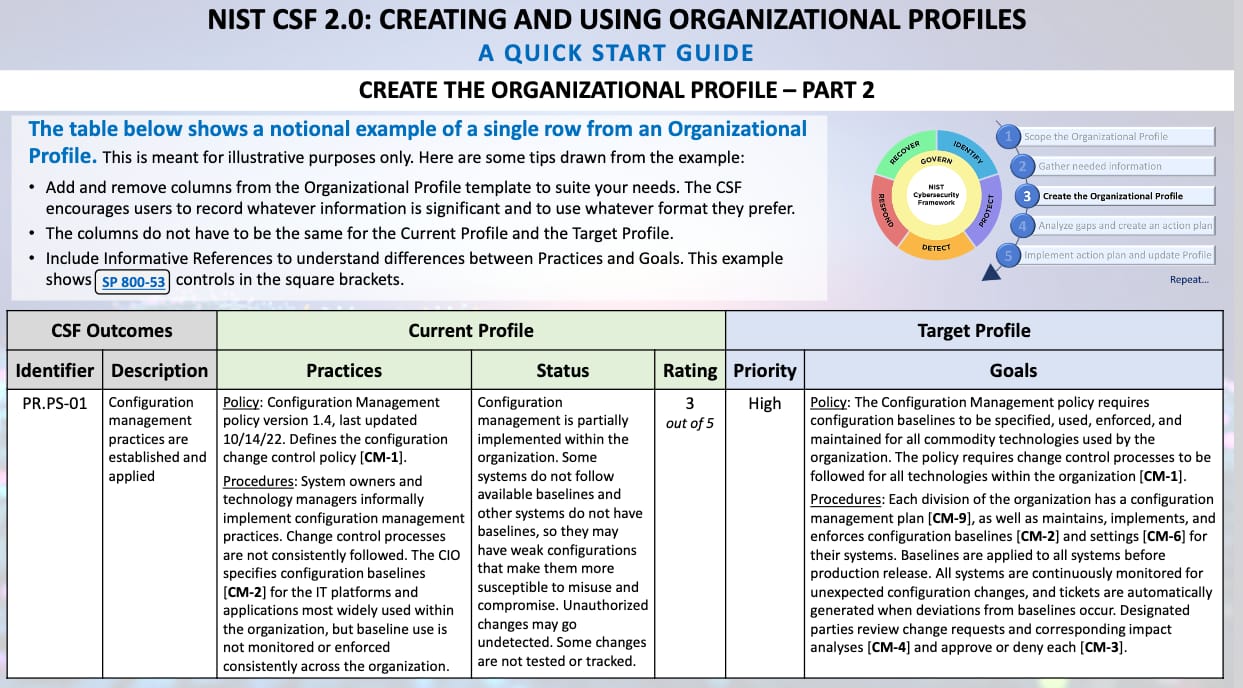
With CSF, the organization has the power to choose the proper controls from any source needed to deliver the outcomes chosen in the target profile
Jason Dion, CPO, AKYLADE
Transcript
Let’s talk about the voluntary nature of the NIST Cybersecurity Framework, with an example.
I’ve seen a number of heated debates on this and it’s a fascinating topic, let’s talk about password complexity requirements.
Is this password secure?
Most people are going to say yes.
- It’s long and strong
- 20 characters, a mix of character types
- Can’t be guessed
If I type it into a password strength testing tool, it tells me it’s strong and would take centuries to crack. https://bitwarden.com/password-strength/#Password-Strength-Testing-Tool
In theory that’s true, but it’s not how it works in the real world.
Password security is not a 2-dimensional problem, that is simply a function of length and complexity, it is a multi-dimensional problem. It is a chain of many links, and only as strong as its weakest link.
Issue 1: it’s hard, maybe impossible to remember, and maybe the person using it doesn’t have a password manager, so they write it down on a sticky note and put it on their monitor, or underneath their keyboard.
Or, they write it in clear text, unencrypted, in a notes app that goes to a third party service provider, or a work app, that their IT administrator can see.
If there’s a malicious employee at the service provider or your company, your credentials can get compromised. Or if their networks get compromised, your password in clear text is now vulnerable to attackers there.
What if you use this same password, with 20 accounts and 20 service providers. If one of those providers has a breach, and shows up at haveibeenpwned.com
A database from a reputable security researcher with more than 700 pwned website, 13 billion pwned accounts
What if it’s been added to the rockyou-20 database of leaked passwords here on GitHub, that’s added to a cracking tool
The list of links in the chain to consider here goes on, there’s a famous hacking tool call Mimikatz that steals password hashes from the memory in windows, and it is indiscriminate, whether that has was created by a strong password and a weak one.
Let’s saw off the list of examples there.
We’re building a business case for multi factor authentication.
And, where prescriptive frameworks can go wrong. Some of them take a 2-dimensional view of passwords. Prescribe 16 characters and don’t persecute MFA.
The organization wants to be compliant and just does 16 character passwords.
Risk is higher now, than if they had 8 characters and MFA. Not a good outcome.
Other options to improve authentication security, other than password length and MFA would be
- Using known password lists, when users create their passwords, don’t allow a known one
- Time based one time passwords
- Geographic and IP restrictions
- Anomaly detection and login monitoring
This is where the true power of the NIST Cybersecurity Framework comes into play because it focuses on a risk based approach to getting the best outcomes, not prescriptive controls.
We have talked before about profiles. Here’s an example from the CSF Quickstart guide, where to get the outcome of, subcategory PR.PS-01, configuration management practices are established and applied. This organization is partially implemented in its current profile.
We have a Configuration Management policy that is up to date. We have procedures that are sometimes followed, but not consistently.
So in our target profile our goal is to make sure baselines are applied to all systems before production release. All systems will be continuously monitored for unexpected configuration changes, and ticket will automatically be generated when deviations from baselines occur.
The key here is that the organization is defining its own outcomes and overseeing its own cybersecurity risks. It has the power to choose the proper controls from any source needed to deliver the outcomes chosen in the organizational target profile
We hit more examples in the next lesson.

