📈 12.15 Part 1: EXCLUSIVE TO SIMPLY CYBER ACADEMY: Analyzing Network Diagrams - Featuring Dr. Gerald Auger!
Contents
📚️ Exam Objective 2.3
🔎 🌐 Review Network Configurations
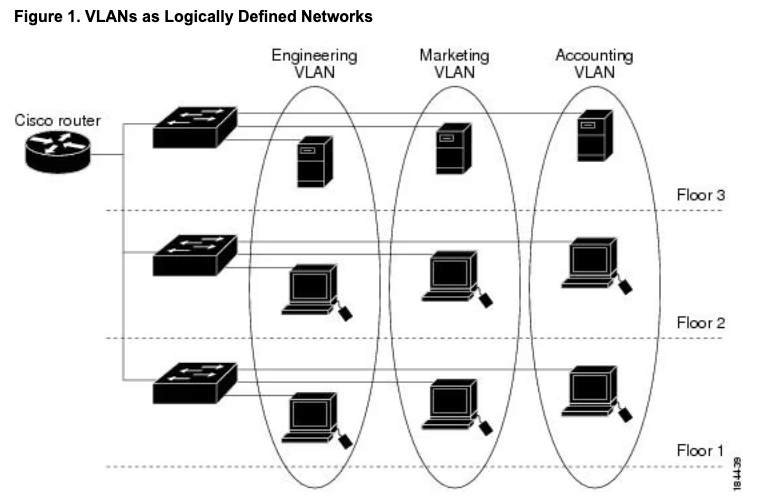
Subnetting/VLAN
Firewall/DMZ

www.cisco.com/c/dam/assets/sol/sb/isa500_emulator/help/guide/ad1681599.html
Virtual Private Networks (VPN)
Cisco: How Virtual Private Networks Work
🔎 🤖 Review Legacy System Configurations
Center for Internet Security Benchmarks
www.cisecurity.org/cis-benchmarks
Transcript
Steve:
Well, hey, Gerry. Thanks for coming back one more time. We're here for the bonus lesson that is not in the Mastering Cyber Resilience textbook, but it is an exam objective and an important topic. And I specifically wanted to call a lifeline and ask for your input on this one, please, because this is one of my weaker areas, frankly, coming from an access and change management-heavy domain of knowledge, and network security is not one of my strong areas, something I'm continually working to improve. And I think what they're saying here is that in our understanding of the business, in addition to having those conversations with everyone, you can glean a lot in terms of where to focus your cyber resilience efforts by looking at some of these network diagrams. So it's okay if I kind of go through these and maybe share my perspective on what I think it means, and then you can coach me and help me understand it?
Gerry:
Yeah, yeah. Just let me know, and I'll chime in as appropriate.
Steve:
Awesome. Okay, well, thank you. So let's take a look here. Step one is reviewing network configurations. So, for example, subnetting and VLANs.
Gerry:
Right. So you know the classic picture: the accounting department is on the accounting subnet, and they're segregated from HR. HR's got that personnel data, and finance has the financial statements, and there's insider trading and other risks. Now, in reality, maybe finance is in financial SaaS, right, and HR's in the human resources management system. But if we stick at looking at an organization's subnetting and VLANs, I think the idea is compartmentalization and trying to limit the blast radius when a host is compromised as much as possible. And then in practice, that's not something that's fairly easy or trivial. It's a lot harder than this picture looks, right? So the idea is to limit blast radius if a host is compromised with subnetting. However, that's actually really hard to do in an environment that wants to collaborate. Over to you. What do you think of this section and what to look for?
Steve:
So, yes, network segmentation is a great technical control for the reasons that you outlined around blast radius. Also for access control, because you can use essentially jump boxes to control a checkpoint or a gate that you can only enter, say, the medical device network segment through a jump box. Same for exfil or egress out of that network segment. So network segmentation is good. Now, there are network segmentation solutions that you can buy and roll out, which are definitely nice. But if you're going to do that, you're going to go whole hog on network access control, like at the NIC itself and posture profiling of the endpoint when you plug it in before you give an IP address. Relative to network segments, you can use VLANs, right? I've seen this before. I get the idea of the textbook of the different departments. In my practice, what I've seen, it's more risk-based than it is departmental, right? Because a business is a business, right? A lot of times you'll have people who are collaborating with different entities across the business. So it doesn't make sense to kind of functionally break it up that way.
Gerry:
But I've seen things like going back to the medical device network segment. So in healthcare, there's these really complicated medical devices that run legacy.
Steve:
IOT. Kind of like an OT network-ish, like IOT devices.
Gerry:
Yeah. That's a great way to put it. It's like OT Lite. So you could have a Windows XP box, a Windows 7. You could even have a Windows 11 fully patched system. But you and your IT department are not allowed legally or contractually to maintain it, right? So the vendor will log in remotely into that box using some type of team viewer, any desk log me in thing, to do maintenance and stuff on that machine. Well, they're coming directly into the deep part of your network through an outbound reverse shell, essentially. So in order to protect yourself from that, you'd want to control what's allowed into that network because there's all sorts of vulnerable systems that you can't patch. So you want to make sure a threat actor moving laterally can't get in there.
Steve:
Also, you've got to think about it holistically. So the other side, if someone compromises, you know, whatever, McMichael Medical Device Technology Company, and then routes in through a remote access solution, kind of like SolarWinds or Kaseya, something like that. You want to make sure, like, it's going to be painful that they're going to have access to all the medical devices, but at least your EHR or your IT operating systems, your accounting, all that, wouldn't be impacted.
Gerry:
So definitely valuable. Also, if you think about it like the old time, this is kind of, I don't even think this is legal anymore, but they used to have these like firewall, like literally they were called firewalls in older buildings that would have like a rope attached to it and it would be on like an angled bar. And if a fire caught was in the room, it would burn the rope, the rope would burn off, and then the door would slide and compartmentalize that room off.
Steve:
It's really bad. Like a submarine, when a submarine gets hit, it has these different compartments that compartmentalize it down.
Gerry:
Yeah, a hundred percent. So you can take advantage of those mechanisms here as well. So if there is like, you know, a compromise or something, you could start shutting down segments of your network while maintaining resiliency of other systems on your network, other endpoints and services. A lot of times what you'll see, unfortunately, is flat, they're called flat networks. And basically there's, you know, a big strong firewall at the egress, right? At the internet-facing asset. And then on the inside, it was once referred to me as an M&M. It's got a hard candy shell.
Steve:
I used a Cadbury egg literally as a photo in the course.
Gerry:
Yeah, a hundred percent. So if you think about that from a flat network, is that bad? No. Is it good? No, it's not as good as network segmentation, but you got to remember, guys, we're GRC professionals. You don't have infinite money. You have to make a decision based on the amount of risk that choosing that, you know, accepting that risk of a flat network brings you. Like you're obviously, if you're a small business, you're not going to get funded for network segmentation. So you can cobble together something, maybe do host-based firewalls on critical servers, right? So you can use IP tables on a Linux box, right? So you could do segmentation, like micro segmentation.
Steve:
But yeah, so yeah, that's what I think about that, Jerry.
Gerry:
So I got to let you know live that in the first minute, I hit two things you taught me in your daily cyber threat briefing in your courses that I applied on the job popped out, okay? Like one is, just like last week, you were saying, if you tell a network engineer to, you got to put MFA on something that's, you know, behind a jump box, because MFA is a good practice. He's going to punch you in the face.
Steve:
Like, I was working on an SRA with a security risk assessment with a network engineer. And it just really made me, really resonated with me. And it helped me, you know, not get punched with, you know, I'm just kidding. Of course, it's my colleague, but it's like, that was good advice for a GRC person to work with.
Gerry:
Yeah, maybe not punched in the face, but you will lose political capital and credibility. It's just, you need to understand, it tells you a lot if you can appreciate why MFA does not make sense in that environment. It's a good like asset test in terms of do you know what you're talking about? And then also, you mentioned in a healthcare type environment, you could have Windows XP on a box. And then the tip I got from you on that, you didn't say it here, but you've said it in the past was like, so don't put email in that box, right? And that's a segmentation and a compartmentalization thing.
Steve:
And I think that, you know, helped me appreciate that concept as well. So that was just cool that, you know, real world examples of your courses that I've applied and now more can apply.
Gerry:
Awesome. Thanks for sharing that!
Steve:
Yeah, well, I mean, this is real stuff, you know!